Information Security | Security Measures
At the Canon Marketing Japan Group (hereafter, the "Canon MJ Group"), we are taking initiatives to reinforce the foundations for information security, which we position as our corporate social responsibility, aiming to build a secure society. We will remain aware of information security risks, including cyberattacks, and continue striving to improve information security by regarding it as an important business challenge.
Security Measures
Promotion Structure
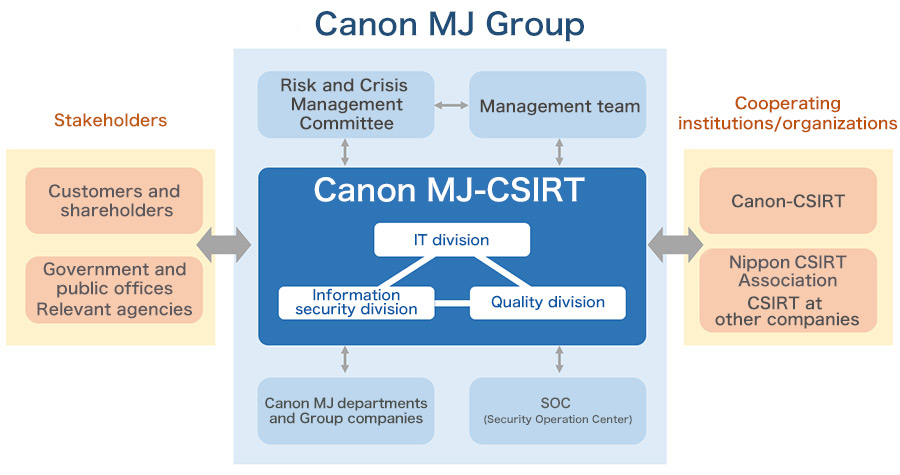
In light of the recent increases in diversity, sophistication, and cleverness of cyberattacks, the Canon MJ Group established the Canon Marketing Japan Group Computer Security Incident Response Team (Canon MJ-CSIRT) in January 2016, and has been promoting activities with the aim of minimizing cybersecurity risks and damage to the Group's internal infrastructure and to products and services supplied to customers.
Canon MJ-CSIRT is organized with members from three divisions within Canon MJ: the IT division, the information security division, and the product and service quality division. Canon MJ-CSIRT operates at the center of the Group, preventing and monitoring for cyberattacks, and mounting a response when attacks occur. Moreover, since it is difficult for one company alone to gather information and research the latest attack and defense methods around cyberattacks, the team collaborates with the Canon Group's CSIRT and other external institutions and organizations, such as the Nippon CSIRT Association.
Specific Measures
Defense against Cyberattacks to Published Websites
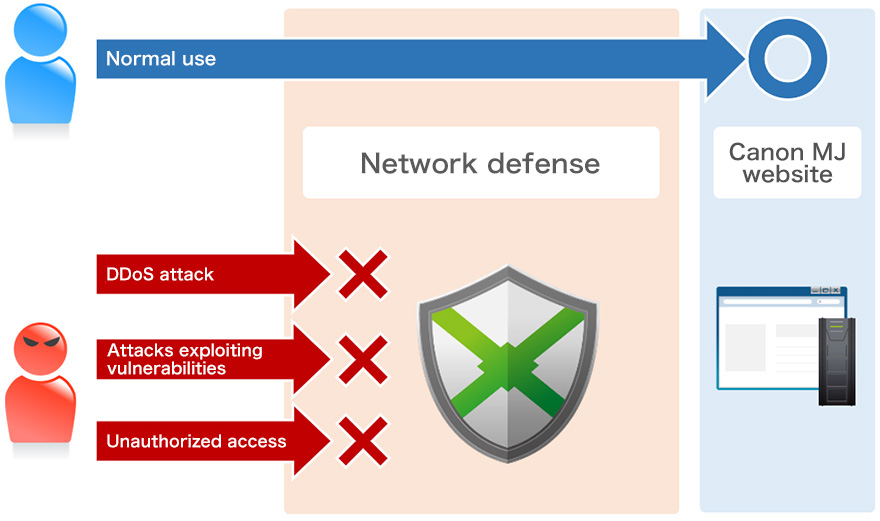
In response to increasingly sophisticated cyberattacks, we take countermeasures based on the concept of defense in depth. For our public website, we not only take traditional countermeasures against unauthorized access but have also introduced measures against DDoS attacks, which are intended to disable a website, as well as measures against attacks aimed at stealing information by exploiting the vulnerability of web applications, instances of which have been increasing rapidly in recent years.
We have built an environment where requests judged to be malicious attacks are blocked before they reach the website, thus securing its safety and allowing customers to use the website with peace of mind.
Establishment of an SOC for Enhancing Security Monitoring and Responses to Incidents
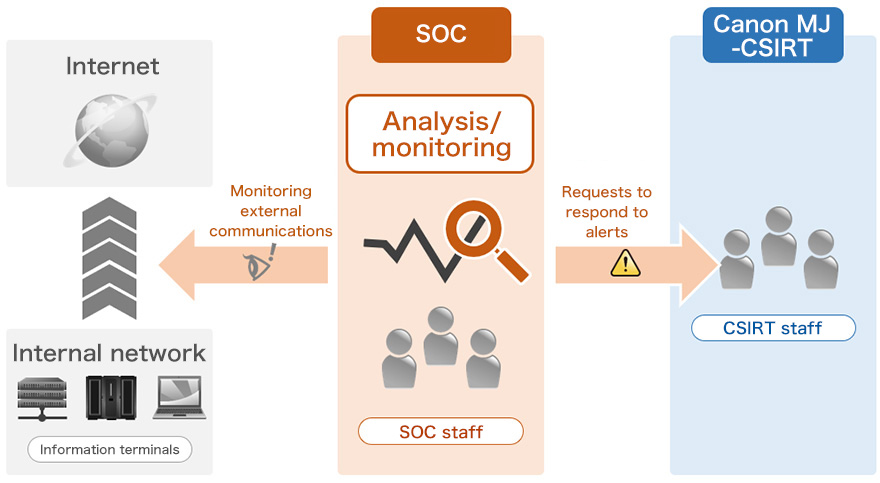
To counter cyberattacks such as targeted attacks and ransomware, it is important to contain the damage as well as to detect the threat immediately. At the Canon MJ Group, we have set up a Security Operation Center (SOC), which monitors information terminals in the internal network and internet communications via the network. We have thus built a system that enables us to discover and detect threats, such as unauthorized access and infections with computer viruses, at an early stage. We have also established a framework in which we minimize damage from incidents by working promptly with Canon MJ-CSIRT in the process from initial response to implementation of a countermeasure, in an effort to enhance our response to incidents.
Information Security Measures
Groupwide IT Control
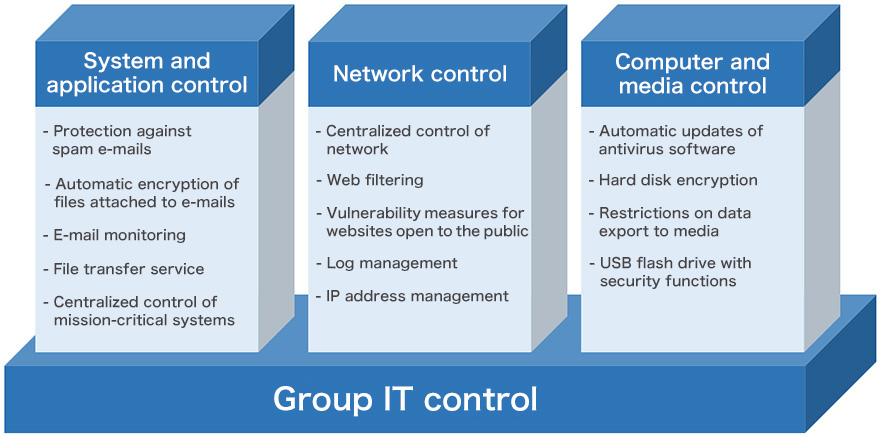
Information leakage occurs in society every day due to cyberattacks and unauthorized access. At the Canon MJ Group, we tackle these threats by performing IT control, such as system and application control, network control, and computer and media control, based on unified IT security policies. This has enabled us to build a safe, secure IT environment with an equal level of countermeasures in the Group and lower operational cost.
Physical Information Security Measures
Use of ID Cards for Access Control and Print Control



In principle, the Canon MJ Group uses a personal authentication system for access control to each business site. We have also introduced flapper gates and biometric authentication as appropriate according to the security level, among other security measures. In addition, we have introduced security cameras to areas accessed by visitors. ID cards for access control are also used for the personal authentication of printer users and for printing log management, which is possible because we have introduced IC Card Authentication PRO for MEAP ADVANCE and Anyplace Print for MEAP ADVANCE from Canon. Personal authentication of printer users has reduced the frequency of incidents where users forget to take printed copies. Combined with the printing log management, the personal authentication has also proved effective for reducing wasteful printing and information leakage risk.
Clear Desk Policy Implemented by Ensuring Thorough 5S

We have specified three of the 12 months in each year as months for enhancing 5S (Seiri for organizing, Seiton for keeping things in order, Seiso for cleaning up, Seiketsu for keeping things clean, and Shitsuke for self discipline) activities, in our effort to ensure and establish thorough 5S of offices and meeting rooms. Moreover, we have continued to implement a clear desk policy by ensuring that employees store PCs and documents in locked wagons or locker boxes and clear the desktop and areas under and around the desk before they leave office for home. We thus strive to reduce the risk of information loss and leakage and manage information assets appropriately.